SEO One Way Links - Recurring Monthly $$$ - Increase Rakings & Sales.
Saturday, December 5, 2009
How I Obtained A Free Computer System
About four years ago I quit my job in order to start my own business. I was committed to starting and operating my business while incurring as little debt as possible. I decided that one area that I could easily save a significant amount of money was with computer systems. In case you haven't heard of it before; Linux is a completely free operating system that can run hundreds of free applications. It was during this time in my life when I was freeing myself from my corporate job in favor of owning my own business, that I also decided to free myself from Windows in favor of Linux. I simply couldn't justify not only paying for basic software, but also all of the third-party anti-virus and spy-ware applications that are required to keep Windows running efficiently.
The first thing you should know about Linux is that it comes in many different “flavors” or “Distributions.” You see, Linux itself is just the core skeleton of the operating system. This is the part that user never really sees, but is the engine behind the scenes that gets everything done. A Distribution, is simply all of the different packages and applications that are bundled on top of that core system that make it more usable for the average user.
I will tell you right now that while I was committed to using Linux full-time, I still had some reservations about Linux's ability to fulfill all of my computing needs. Therefore, I chose to set up my computer as a dual-boot machine. This means that I installed Linux on a section of the hard-drive next to Windows. Then every time I started the computer it gave me the option of booting into Windows or booting into Linux. Over time, as I became more and more comfortable with Linux, I used Windows less and less.
I first started tinkering with Linux about ten years ago. During that time I have tested many different Distributions and have come to the conclusion that Ubuntu is the best Distribution for me and the average Windows user. You see, Ubuntu has a very simple installation process, many different completely free applications that are easily installed and very good hardware driver support. Ubuntu also adheres to a strict six-month update schedule which provides completely free upgrades every April and October.
So how did I get the free computer mentioned in the title of this article? I simply let it be known to friends, co-workers, acquaintances that I was willing to dispose of any “dysfunctional” Windows PCs that they may have. Almost all of the time there was nothing really wrong with the hard-ware of these machines. Windows had simply become unusable for one reason or another. By installing Ubuntu, I was able to resurrect the machines while spending zero dollars. Now I have an office with six Ubuntu machines and the kicker is that people also throw away perfectly good printers, so I have four of those as well.
If you are unsure whether or not you can live without Windows but would like to give it a try, you can visit http://www.trybuntu.com and get a 19 page illustrated step-by-step guide to setting up your PC as a dual boot machine. If you are already a Ubuntu user you can utilize this script ( http://www.trybuntu.com/EnableScript.txt ) to fully enable new Ubuntu installations.
You too can achieve complete computing freedom and a completely free PC with Ubuntu.
About The Author
Joe Gillis began experimenting with Linux 10 years ago. Since that time, he has tried Linux distributions by: Red Hat, Knoppix, Linspire, Puppy, Damn Small Linux, Linux Mint, Debian, Fedora and Slax. A little over three years ago he installed Ubuntu on his Dell laptop and has never gone back to Windows.
Joe decided Ubuntu was the best distribution for him because of the proprietary hardware driver support and it being a Debian based system. Debian is a completely community driven project and supports one of the largest collection of processor architectures. Also, the Debian Apt-Get package management system is very user-friendly.
Since becoming an exclusive Ubuntu/Linux user, one of Joe's passions is converting others to Linux as well. "A Newbies Guide To Installing Ubuntu" is one of his contributions to that effort.
Tuesday, December 1, 2009
Want To Create A Computer Based Home Business?
Is a Computer Based Home Business Right For You?
Did you ever think to have a http://computer-based-home-business.com/? If so, are you determining on how to obtain a n outstanding income and could this be adequate to deal with all your expenses or can cover up all your retirement dreams? Generally in every home business, financial independence doesn't come into an instant effect. There are still lots of methods that must be taken into consideration and an additional effort that you must do before you can absolutely become successful in your computer based home business. Whether you are promoting your own products, promoting e-books or bid for some important service, you have to take some home business considerations.
Do Your Homework
When you are deciding to establish a computer based home business, you may consider to have a business in a box type of application. In effect, there are numbers of programs available that will authorize you to easily learn how to market a service or product that is established by somebody else. This may be a perfect idea.This may, but be smart to research the concept because there are several of these sorts of companies that may say it is easy to make money from this. When it comes down to it, you'll be learning advertising and trying to work out how to get the potential customers to buy or avail your service or product.
As with any usual business, look into the sort of investment needed. There are various franchises and even small businesses I know, that have need of a huge amount of funds to begin and might take years to come out quits.
Look for the best computer based home business that will fit with your way of life. You must also consider your family in some decision making in your business, so you can get other ideas or concepts that you may use to proceed to your business. In this way, you can also spend your time with your family. If you love what you are doing, you can be successful and can create the autonomy that you wanted to have.
Is your personality matches your new business?
When you plan to have a computer based home business, you should always plan for a business that will suit your personality.In this way, you are assuring yourself to be successful in your chosen career. If you are having fun in sales, then you may consider picking a company that allows you to interrelate with various people through phone, email or maybe in some networking affair. This sort of company may be a direct sale of product or services to the end purchaser or some kind of business-to-business sales.
If you aim to stay with your computer based home business and don't want to leave your web community, try to sell goods and become an associate. In other words preparing an internet site that draws people to it and sells to them employing a shopping cart or a service based company. If you want this plan, you will need to set up more than one site.
The Computer Based Home Business Myth
When you manage your own business, you don't have to just sit back and relax and wait for your earnings to come. It requires you to do some additional work for your business to be successful. As you go along, you will observe that sooner or later, things will become more simpler to deal with. Compare obtaining a business who just started to run, with getting the shuttle off the ground. It will take a maximum effort to start, but as you commence to get the ball rolling it would become easier.
A large amount of individuals still being misled by all the publicity and deceitful claims of earning money in a quick and simplest way. If you need to earn more and to be successful in your computer based home business, you have to work hard to get your objective. With a lot of companies offering their services to support you run your own business, remember that not all of the services offered will fit your needs. You have to do some further research and shop around. Also if you launch your business plan and set a useful daily set of purposes you'll be in a point to get off the ground faster.
If you sincerely working hard for your computer based home business or any other kind of home business you want, you are certain that you are capable to have a http://www.mybigkidincome.com/ that will carry on to draw in a monthly income for all your hard work.
Creating a Stable Income
Once you catch your target marketing niche, which is another subject, you have to identify whether you will continue to sell product to new prospects or whether you can just do the constant thing in order to create a secure flow of income. Take advantage of technology and you may choose to use several automated programs and systems that will authorize you to create a large result in your target market.
This can be a straightforward posting of articles related to your theme. The articles must discuss everything about what you need individuals to learn about your product or service and how will they benefit from this. In this way, you are definitely inviting people to try or purchase your product or service. If your article hold so much important information, it'll get pick up by other website users and go round the net with your link back to your site. Sounds good isn't?
Try to obtain a product or service that can be sold in a sequence or in a monthly basis, for it will support you to gain an Automated income stream.
Boost Your Education and Boost Your Commitment
Absolutely, you required to be more educated and must be more aware of all the products or services that you are promoting in the market. You can promote and sell your products or services well if you are familiar with it, how it works, and how it help you personally. For instance, if you are promoting books or tapes or Cd's produced by other person,be sure that you know the details of the products you are selling. Or if you are promoting and selling services, be sure you know how your potential clients will benefit from them and how this particular service differs from the others.
There are so many marketing tools and home study trainings that will assist you boost your skills about the computer based home business that you wanted to run. To be successful in your chosen business, you must well educate inform yourself about the business you need and also take some consideration of having a computer based home business training before starting your business.
By following these guidelines, you are certain that you can create a http://www.computer-based-home-business.com/ that will really fit your personality and your needs. This will surely free you from working 9 to 5 daily.
About The Author
After spending the last few years in every marketing training that I could find, I believe this to be the best of the best super funded proposal and internet marketing training site. Learn how to create powerful residual monthly income at http://www.mybigkidincome.com/.
Google Analytics - Keyword Positions
One of the biggest questions advertisers have when manage their pay per click account is how much they should bid for their keywords. Bidding too high may incur too much cost and advertisers might not be able to sustain a profitable ROI, whether bidding too low might not allow their ads to be positioned at a visible spot.
There is a function in Google Analytics that allows advertisers to see at which positions their keywords receive the most visits, transactions, revenue, conversion rate, and etc.
Simply login into Google Analytics, select a report which has the proper filters applied. Then click on Traffic Sources. Within the expended pull down menu, select Adwords then click on Keyword Positions.
Now just type in the keyword that you want to analyze into the “Find keywords” box to see the stats on that keyword. Click on the keyword once, then you can start seeing the position break down on the right.
This handy little tool might not be practical for huge companies that have tens and thousands of keywords, since manually analyzing each single one of them would just be overly time consuming. But for small businesses that have a few core keywords which make up the majority of their conversions, this is a great way to get some general ideas on how much they should bid to maximize their investments.
One thing to be careful though, is not to solely rely on the number of transactions to make decisions; instead you should also take the conversion rate, and number of visits into account.
For example: let’s assume for the time period you are analyzing, your keyword have spent 90% of the time at position one and only 10% of the time at position three, so most likely there would be more transactions happening at position one than at position three.
But at the same time, the keyword might only be getting a 0.3% conversion rate at position one whereas at position three, it might be getting a 3.2% conversion rate. Assuming there isn’t a big different on the number of visits between the two positions, it actually makes more sense to lower your bid and have the keyword on position three for most of the time.
As with any other analysis process, make sure you have a sufficient data collection before making any judgements.
About The Author
Pitstop Media is a Vancouver based company, providing Internet marketing services. We offer SEO Vancouver services, PPC Vancouver Services, google analytics services to companies of all sizes, from start-ups to corporations. Please contact us at http://www.pitstopmedia.com if you need assistance.
Friday, November 27, 2009
Bye-Bye Pop-Ups And Computer Slowdowns! Learn More About Spyware Removal
‘Spyware’ is a form of advertising software that is covertly installed on a person’s personal computer without their knowledge or consent. Some advertising software today is put in with the permission of the computer owner as a form of payment for the use of a website or program, and these forms of marketing software are usually termed ‘adware’.
The difference between spyware and adware is knowledge and consent of the user. Because spyware is added without consent, and often can lead to a number of damaging effects to a computer, spyware removal is a popular subject for computer users today.
The first step in spyware removal is of course determining that you indeed have spyware installed on your computer. Chances are, you do. In a study conducted by America Online and the National Cyber Security Alliance in 2004, it was estimated that 80% of computer users across the world have some form of spyware installed on their computer, and 90% of these users are not aware of it.
Some common signs that your computer maybe dirty with spyware are ‘pop up’ advertisements that occur frequently and sometimes even when you are not on the web. These ads can be extremely irritating to be sure, but spyware can have even more disturbing effects to your computer. For instance, it can considerably slow your computer down, add hard to remove toolbars to your browser, change your home page without your knowledge, and cause put away or break down, resulting in lost data.
The good news is there are a number of spyware removal programs available that will scan your computer to detect spyware elements. If it is determined that your computer is infected with spyware, some of these programs are able to remove the infection.
Many spyware removal programs are available free of charge, though they must be updated regularly. Some programs will allow you to scan your computer for free, but will then ask for payment in order to clean the identified spyware. Personally, I’m a little disbelieving of these programs, and stick to the ones that are entirely free of cost. Some good examples include SpyBot, and AdAware.
These spyware removal programs are usually able to get most spyware off your computer. To increase your chances, it is best to run two or even three different programs. You may encounter occasional spyware programs that are especially hateful and will require more complicated measures to remove. Instructions on how to remove these more deceitful spyware programs are often available in technical meeting across the internet, and most stores that offer computer repair are also able to clean spyware as well as viruses.
About The Author
Paul I. Etkin provides readers with up-to-date commentaries, articles on http://www.a1computermagazine.com, http://www.computingguidezone.com, as well as business related information.
Microsoft Money Investment Recordkeeping Tricks
Microsoft Money provides powerful investment record-keeping tools for individual investors. Unfortunately, once you step beyond investments like stocks, bonds, and mutual funds, the mechanics can get a little tricky. Here are some tips for handling common investments in Money.
Certificate of deposits
If you purchase a certificate of deposit, you can treat it in the same way that you treat a bond purchase. Basically, certificates of deposits, or CDs, are just bonds issued by banks or financial institutions often for a shorter period of time. For example, you can think of a two-year CD as equivalent to a two-year bond.
Zero coupon bonds
If you invest in bonds, you may know that some bonds don’t actually pay periodic interest. Instead, these bonds, called zero coupon bonds, pay their interest when the bond matures. For zero coupon bonds, you need to annually accrue the interest on the bonds. The annual interest needs to be accrued because, by convention, you report the annual increase in the zero coupon bond’s value as interest earned.
To record accrued interest on a zero coupon bond, record bond interest that accrues in the normal way. In other words, whatever amount shows as being accrued—this should appear on the statement from your broker—record it as bond interest income.
After you record the bond interest that’s accrued, you need to record a return of capital transaction that adds this accrued interest back to the value of the bond. The amount of this capital transaction, obviously, needs to equal the accrued interest amount. But there is a twist here: You need to specify the return of capital amount as a negative value. For example, if you accrue $100 of interest on a zero coupon bond, you also need to record a return of capital transaction for the bond equal to –$100.
By recording the return of capital transaction, you in effect transfer the bond interest money from the associated cash account and add it back to the zero coupon bond’s value. In this way the associated cash account shows the correct cash balance and the zero-coupon bond shows the correct cost basis. The zero coupon bond’s cash basis equals the original purchase price plus all the accrued interest that’s been recorded to date.
Derivatives
Derivatives are securities that derive their value from some underlying security. For example, an option to sell a stock, called a put, is a derivative. It derives its value from the underlying security. Another derivative is an option to buy a stock, called a call. You can use Money to keep records of derivatives, such as puts and calls you buy.
In general, derivative record-keeping is quite straightforward. If you buy a derivative, say a put or a call, and later sell the derivative, you simply have a normal investment transaction. You treat the purchase and later the sale in the same way that you treat the purchase and sale of any stock. If you make money, you realize a gain. If you lose money, you realize a loss.
If you buy or sell a put or call and hold the option until it expires, things work almost the same way. However, in this special case, you do need to record a Final Sale transaction, and the sales price is zero. Obviously, if you hold a put or call until it expires, you don’t actually sell the derivative. But you need to record a sale transaction to reflect the fact that the option is no longer worth anything.
These are the basic techniques you need to know for put and call record keeping—and record keeping for similar derivatives—but there are two special circumstances in which more complicated record keeping is required.
Selling Puts and Calls
If you sell puts and calls—note that the earlier discussion involves you in investing puts and calls—you need to record the option as a regular buy or sell transaction. In other words, if you sell a put and the person to whom you sell it exercises the put, you record this transaction as a regular sales transaction. Similarly, if you sell a call, you record the transaction as a regular buy transaction.
If you sell a put or call option and the option never gets exercised, you record the amount of money the buyer pays you as Other Income.
Exercising Puts and Calls
Typically, individual investors don’t actually exercise puts and calls that they buy. Instead, they simply sell the option back to the broker. However, you might end up exercising a put or call, and in this case, you need to perform special record keeping.
To record the exercise of a put option, record the sale of the put option at a price equal to zero. This zero-value sale is how you record the expiration of the option. After you have recorded the expiration of the option, you record the sale of the stock in the same way that you record the sale of any stock. (Remember that a put is an option to sell stock.)
To record the exercise of a call option, record the sale of the call option at a price equal to zero. This zero-value price lets you record the expiration of the option. After you have recorded the expiration, you record a regular buy transaction. (Remember that a call option is an option to buy a security.)
Precious metals and commodities
You can treat investments in gold and other precious metals, gold coins, agricultural items, and other commodities in the same way that you treat shares of stock. Rather than entering a share price, you enter a price per ounce or a price per bushel. And rather than recording a specific number of shares, you enter a specific number of whatever unit of measure is used to describe the commodity.
In the case of gold, for example, you might enter the number of ounces. In the case of an agricultural item, you might enter the number of bushels.
You can treat options to buy or sell commodities in the same way that you treat options to buy or sell securities. The earlier discussion on handling call and put options discusses the techniques you use for this record keeping.
About The Author
Seattle CPA Stephen L. Nelson is the author of Quicken for Dummies, The Microsoft Money Guide to Personal Finance, and more than 100 other books as well. Nelson holds an MBA in Finance and an MS in taxation. His web site is http://www.stephenlnelson.com.
Tuesday, November 24, 2009
How To Format your Computer
When you format a hard drive you'll lose all the information stored on that drive. Make sure to back your data up before continuing. Insure that you have the discs for any applications or third party hardware you use since you will need to re-install your programs and drivers after re-installing Windows.
Disconnect any external drivers that may be attached to the computer (like flash drivers for example, I forgot to remove a flash driver when was formatting my PC and guess what? I ended up formatting everything including my flash driver consequently losing all the data that was stored in it).
- Insert your installation disk in your CD drive.
- Reboot your PC
- 3.When rebooting, you'll be prompted with “Press any key to boot from CD..” press any key to do so.
5. A License Agreement will appear, press F8 to accept it.
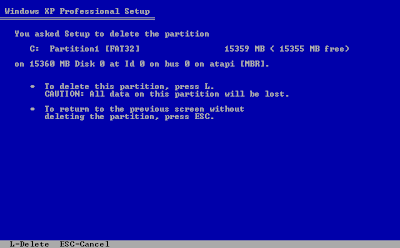
6. This is where you can delete partitions and format drives. On the bottom half of the screen it'll show all your drives and the partitions that exist on them. Use the Up and Down arrow keys to highlight your “C:” partition and press the 'D' key (if all that shows up is “Unpartitioned space” and you have no C: or D: partitions, skip this step).
9. On the next screen press the 'L' key to finalize deleting the partition.
10. You will be returned to the partition list. Highlight the Unpartitioned space item in the list and press C to create a new partition.
11. Windows Setup will ask you for the size of the partition. The field shows the size of your hard drive. Just press "Enter".
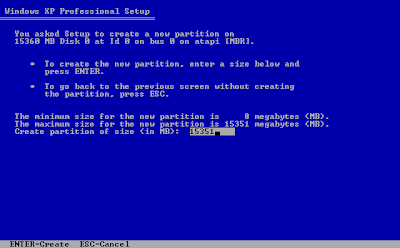
12. Next screen should be showing the new partition C:Partition (New
Highlight it and then press Enter
13. Select the format you want to use, I suggest that you use NTFS (Either one)
14. The next page shows your hard drive being formatted, it will take several minutes.
15. Setup now will be copying important files from your CD.
16. Now remove your disk and then press Enter.
17. Windows Setup program will install Windows and configure your hardware. Now just follow the instructions on the screen. (you'll need the windows serial number)
Good Luck!!!
Computer Repair Done Right For FREE
This article will help users to perform a complete computer cleanup, which will improve the overall performance of their computers. It's not meant as a substitute for regular computer maintenance, performed by a professional computer technician.
Almost every computer user knows that, from time to time, your computer starts to run a little slower or you notice that you hard drive space is dwindling. So many people shrug this off and choose not to do anything about it. They think that it's normal to have these kinds of computer problems and that there isn't anything they can do about it. Your computer is trying to tell you something...it's time for a cleaning. It's time to clean up the junk and organize the files on your computer, just as you would clean and organize your office.
This step-by-step tutorial will put you on the path toward a cleaner, more efficient computer. You'll learn how to perform a complete computer cleanup and you just may save yourself some money, in the future, by maintaining your computer, instead of just taking it to a repair technician when it breaks.
In this tutorial, we'll only concern ourselves with Windows XP (I guess I'll have to re-write this article for Vista), for a couple of reasons.
Microsoft has ended support for Windows 98, 98SE and Millennium.
If you still have one of those earlier operating systems, your computer is just too old to become "efficient" by today's standards.
Follow these cleanup steps and you just may learn to love your computer, again.
Unused User Accounts If you have any User Accounts that are no longer active, logon as a computer administrator and remove them.
1.Click START, then CONTROL PANEL. 2.When the Control Panel opens, click USER ACCOUNTS. 3.Click CHANGE AN ACCOUNT. 4.Click on the name of the account you want to remove. 5.Click REMOVE THIS ACCOUNT. 6.When given the option to "delete files" or "keep files", choose to delete them. 7.After removing all unused User Accounts, restart the computer. Windows Updates Make sure you have all of the latest Windows Updates installed by visiting update.microsoft.com and following the instructions on the website.
It's critical that you keep your computer up-to-date. Microsoft releases new security updates all the time and it's easier just to set your computer to automatically download and install these updates. Here's how to do that:
1.Right-click on MY COMPUTER. 2.Click PROPERTIES. 3.Click the AUTOMATIC UPDATES tab (reference the illustration, below). 4.Choose "Automatic (recommended)". 5.Click APPLY and OK.
Remove Unused Programs This is pretty basic stuff. Most Windows users have already been through the steps of adding and removing programs, but we'll list the steps for those who haven't.
1.Click START, then CONTROL PANEL.
2.Double-click ADD OR REMOVE PROGRAMS.
3.When the window that opens has fully loaded, scroll through the list of programs and remove any that are unwanted or no longer used.
4.Just a piece of advice...any programs listed that mention anything about "bargain", "cash", "search", "web" or "fun", in the program name, should probably be removed.
Temporary File Cleanup Temporary files are one of the biggest wastes of hard drive space, hogs of computer resources and major causes of recurring spyware and virus infections. They need to be cleaned on a regular basis. Follow these steps to remove ALL temporary files from your computer:
1.Double-click MY COMPUTER. 2.Open the root drive (usually C:). 3.Open DOCUMENTS AND SETTINGS. 4.Click TOOLS, then FOLDER OPTIONS. 5.Click the VIEW tab (reference the illustration, below). 6.Under "Hidden files and folders", click "SHOW HIDDEN FILES AND FOLDERS". 7.Uncheck "HIDE EXTENSIONS FOR KNOWN FILE TYPES". 8.Uncheck "HIDE PROTECTED OPERATING SYSTEM FILES (RECOMMENDED)". 9.When the warning message pops up, click YES. 10.Click APPLY, then OK.
***It's recommended that you change the file folder settings back to their default settings after you fully complete the computer cleanup.***
1.With the Documents And Settings folder opened, open a user account folder. 2.Open the LOCAL SETTINGS folder. 3.Open the TEMP folder. 4.Press CTRL+A to select all files. 5.Press SHIFT+DEL to permanently delete all selected files. *Note*: you may be unable to delete ALL of the files and folders because some of them may be "locked" by the operating system or another program. Select smaller groups of folders or files in order to remove as many as possible. 6.Navigate back to the LOCAL SETTINGS folder. 7.Open the TEMPORARY INTERNET FILES folder. 8.Repeat steps 4 and 5. See *Note*. 9.Repeat steps 1 through 8 for all user account folders. 10.Empty the RECYCLE BIN and restart the computer.
Virus And Spyware Scans If you don't already have an antivirus program and two or three antispyware programs installed and updated on your computer, then you're BEGGING for problems. I use Webroot Antivirus/Antispyware and Spybot Search & Destroy (free). If you're relying solely on "free" programs for your computer security, you're likely making a big mistake. I understand that you don't want to pay for software. Nobody does. You just have to look at the value in investing a little bit of money toward preventing the problems that might arise from choosing the "cheaper route". Ok...enough said on that subject.
The most efficient way for antivirus and antispyware products to complete their scans successfully is to run them while the computer is in Safe Mode. To restart Windows in Safe Mode, tap the F8 key about every half-second or so, at computer startup, once you see the manufacturer's logo. You'll then be brought to a screen where you will use the arrow keys to choose the boot mode. Use the arrow up or down key to choose SAFE MODE. Press enter and let Windows do it's thing. When the computer has fully booted, complete FULL SYSTEM scans with your antivirus and antispyware programs. When they are completed, reboot the computer, normally.
Defragment The Hard drive(s) This is the final step in your major computer cleaning. This will insure that the files on the disk are organized in such a way that makes them more quickly accessible, causing less "wait time" and less wear and tear on your drive.
1.Click START. 2.Navigate through ALL PROGRAMS to get to the ACCESSORIES folder. 3.Choose SYSTEM TOOLS. 4.Choose DISK DEFRAGMENTER. 5.Select the main disk (C:). 6.You shouldn't need to "analyze" the drive. At this point, it's better just to choose "DEFRAGMENT". 7.Let the program run through the process and reboot the computer, normally, when completed.
That's it! You should see a HUGE improvement in the performance of your computer.
For More Computer help or advice please Visit http://www.rescuetech.ca
James Perrin
Rescuetech.ca
About The Author
James PerrinRescuetech.ca
Monday, November 23, 2009
Saturday, November 21, 2009
How to Troubleshoot a Linksys Wireless Router
Restart your computer after every step to see if it will work. You don't necessarily need to go down through every single step, if it works.
(Example) Try Step 1 first. If it works for you, you don't need to go on to the next one. But maybe the first step doesn't work. Just try the next one until you find something that works for you.
Follow these steps if you can't connect to the Internet and/or are getting IP conflict:
1.Check if your router is connected to the cable modem using Ethernet cables
2.Unplug the power cables of your modem and router (gateway) for 10 seconds and plug back on
3.Check all your computers to see if they are set up to obtain IP address automatically.To do so go to:
a.)Start menu->Control Panel->Network connections
b.)Right click on Network connections and scroll down and click on properties
c.)On the general tab, Make sure that the box for internet protocol (TCP/IP) is checked. Highlight it and click properties.
d.)When the TCP/IP box opens, on the general tab check the obtain IP address automatically and obtain DNS address automatically. Click OK to exit.
Repair the Connection
4. On the network connections, right-click on your wireless connection (or usually an image of a single computer at the bottom right corner of your computer screen) and click "Repair." The computer will attempt to reconnect to the wireless router.
5.If that does not work go to the router web utility.
a.) On your web browser type your router IP address. You can find it on the router's manual and on the router itself. If you can find try using 192.168.0.1 or 192.168.1.1 or 192.168.24.1 (Usually these are the default IP .)You must do this on the computer that is directly connected to the router.
After it loads, should look like something this:
a.)On the basic setup under setup tab make sure the first box displays Automatically Configuration-DHCP
b.)Scroll down on the network setup enable the DHCP server, then save your settings.
6. Change the channel:
a.)Click on the "wireless Tab", then "Basic Wireless Settings"
b.) the "Channel" page opens, in that area, click on the drop down list and use only channels 1, 6, or 11. These channels do not "Overlap" with any other channels, and will give the clearest signal.
c.)Save your settings.
Thursday, November 19, 2009
Free virus software!
Check your cable provider if they offer this service.
I know that Cox you can add up to 3 PCS and Comcast up to 7 PCS.
To download it, just go to the cable company's website
Before you install:
Please be sure to take the following actions:
* Disable pop-up blockers
* Confirm that your IE browser security is set to Medium
* Uninstall any existing security software
* View complete instructions on these steps and the download process Learn More
Review the minimum system requirements.
Have your cable provider email address and password ready:
* If you are not already signed into your provider, you will be required to sign-in continue.
* Be sure to have a different email address for each new computer you plan to download McAfee to. (For Comcast)
Wednesday, November 18, 2009
How to uninstall Programs
Windows XP
1. Click Start.
2. Click Control Panel.
3. Double-click Add or Remove Programs.
4. Locate and click the application you want to remove.
5. Click Remove.
6. Follow the prompts to uninstall the software and restart your computer if necessary.
Windows Vista
1. Click the Windows button.
2. Click Control Panel.
3. Double-click Programs and Features.
4. Locate and click the application you want to remove.
5. Click Uninstall.
6. Follow the prompts to uninstall the software and restart your computer if necessary.
*Some security software (anti-virus, firewalls, etc.) will not function correctly with other similar programs installed. Uninstalling previous security software, including any existing McAfee programs, should prevent any conflicts from occurring during or after installation.
Disable popup blockers
Internet Explorer
1. In Internet Explorer, click Tools.
2. Click Popup Blocker.
3. Select Turn Off Popup Blocker.
Browser Toolbars
Most toolbars such as the Google Toolbar or Yahoo Toolbar have a built-in pop-up blocker. These should also be turned off or disabled temporarily before attempting to install McAfee products. Each toolbar has different settings for turning off the pop-up blocker, but most can be accessed from the Settings or Options menus on the toolbar.
Other Popup Blockers
Most pop-up blockers can be disabled temporarily by holding the Control key (CTRL) on your keyboard while clicking the button or link to begin the download and installation process.
Disable Script Debugging
1. In Internet Explorer, click Tools and select Internet Options.
2. Select the Advanced tab.
3. Under Browsing, select Disable script debugging (Internet Explorer) and Disable script debugging (other).
4. Click OK.
Enable SSL 2.0 and SSL 3.0 certificates
1. In Internet Explorer, click Tools and select Internet Options.
2. Select the Advanced tab.
3. In the Settings box, scroll to the bottom of the list under the header item Security.
4. Select both Use SSL 2.0 and Use SSL 3.0.
5. Click OK.
Mozilla Firefox
1. In Firefox, click Tools and select Options.
2. Select Advanced.
3. Select the Encryption tab.
4. Under Protocols, select Use SSL 3.0.
5. Click OK.
Delete Temporary Internet Files and Cookies
1. Open Internet Explorer.
2. Click Tools and select Internet Options.
3. Under Browsing History, click Delete (for Internet Explorer 6, this is on the General tab of the Internet Options dialog).
4. Under Cookies, click Delete cookies.
5. Under Temporary Internet Files, click Delete files.
6. Click Close, then OK.
Mozilla Firefox
1. Open Mozilla Firefox.
2. Click Tools and select Clear Private Data.
3. Select the boxes next to Cache and Offline Website Data and Delete cookies, then click Clear Private Data Now.
Tuesday, November 17, 2009
Earn Lucrative Profits By Learning Adsense Secrets
Internet is an excellent venue for thousands of business opportunities. You can sell your own product, earn profits or market affiliate product in the web and get commission. Adsense is a wonderful option for generating more online profits, no matter whether you have a small or large website.
Adsense ads are similar to Adword ads, but the former has a great impact in the affiliate marketing sphere. There are several advantages in joining Google Adsense;
•Adsense is too simple and free to join
•You can easily paste a bit of adsense code into your pages.
•You need not spend more time and effort in finding advertisers.
•Google can provide you highly relevant ads that match the content on your web pages.
•It helps you to save more time, as you are relieved from the problem of selecting different ads for various pages.
•Adsense is ideal for you, if you are a beginner internet marketer. You can use it even if you are an expert, as it offers the best possible way to earn more profits.
•As Google is responsible for finding the best ads for your page, you can pay more attention to provide well written content.
•Adsense provides easy to understand stats and you would not find any trouble in recognizing them.
•Adsense allows you to filter up to 200 URLs. You can block ads, which you find less qualified for your site.
•Adsense is suitable for you, if you own a single small website. You can simply apply a bit of code into your site and can get relevant text ads on your pages almost instantly.
•It is also perfect, if you own several sites, as you need to apply the code only once.
Though Adsense offers several advantages, it has a flip side also. However, you can overcome such problems easily, if you learn the basics of making money with Google Adsense. You can then start making huge online profits. You can find some resources in the internet that teach you Adsense secrets. You can learn how to use the latest techniques that help maximize your Adsense potential.
Adsense is an effective way to increase your traffic and understanding it better can help you run your online business more profitably. If the advertisers are willing to pay more per click, you can earn more. You need to find out the niche advertisers who are ready to spend more money. The most effectual method to find the niche advertiser is to research the keywords. It is worth deciding on finding keywords that have an average cpc ranging from $18 to $20. The high rated keywords in this range are credit card, free credit reports, website hosting and consolidate debt. You need to work hard in order to find which one would be suitable for an Adsense monetized site.
If you want to earn lucrative profits using Adsense, you need to put forth your efforts to find and use effective, targeted keywords. If you know the buzz words related to a particular product or market, you can then create a word list easily. However, if you cannot create such list, you need to use software, which helps to define appropriate keywords. It is also important to use the words that link to the product or service that you are marketing.
You can increase your Adsense revenue by using channels. You can use logical channel names to distinguish several ad units. You can use URL channels to determine the performance of your web pages and to get an understanding about the performance of your sub domains.
Some internet marketers struggle to earn money with Adsense, as they do not know the right techniques. On the other hand, there are some marketers who make substantial money with Adsense alone. You can gain more profits without spending more time by using the appropriate Adsense techniques. You can double or triple your income by placing ads on your sites. You can spend more time with your family and friends leaving all the work to your Adsense site to earn good profits. However, you need to take some efforts to find the techniques that really work.
About The Author
Taylor Hutchison-Brown is an Internet Marketer who loves to share his knowledge, skills and experience. If you would like to learn more about Earn Lucrative Profits By Learning Adsense Secrets or other Internet Money Making principles, strategies and resources as well as tips on monetizing your online business visit "instantinfoproducts101.com" now!
Copyright C 2009 Taylor Hutchison-Brown, All Rights Reserved.
This article may be freely distributed without modification and provided that the copyright notice and author information remains intact.
The author invites you to visit:
http://www.instantinfoproducts101.com
Article Source:
http://www.articlecity.com
Basic Explanation of Hyperlink Types
This article deals with the basic classifications of links. Links can be broken into many categories and types, and having the basic knowledge of what each category means is important. This article does not go heavily into actual linking strategies, since that is a far broader subject.
Reciprocal Links
Reciprocal linking is a classic and very common type of link. Also known sometimes as two ways linking, it is basically the process of link trading with other webmasters. It's the whole idea of 'You link to me, and I’ll link to you'. Oftentimes you will see websites with a 'links' page someplace on their site, often buried at the bottom someplace. These pages are filled with various links to other sites that hopefully have something sort of in common with the site you’re visiting.
Reciprocal links are falling somewhat out of fashion lately in favor of one way links, which are considered more powerful, and requiring less maintenance. It is widely thought that the search engines recognize the links are reciprocal ones and give the link somewhat less weight than if it was just a one way incoming link. One other issue with reciprocal linking is that once you setup a reciprocal link with another webmaster, you have to return to their site occasionally to check and make sure your link is still actually there. Overall this is still a powerful way to get links however and should not be overlooked.
One Way Links
One way links are links that are incoming to your site, but are different than reciprocal links in that you don't have an outgoing link back out to the site that linked to you. For instance if I throw up a link to the Google homepage, that’s a one way link to Google. They are not putting a link on their homepage back to here, though wouldn't that be nice! This is essentially the most basic type of linking there is, but it can also be the most powerful.
When the search engines go through someone’s site and see a link to your site, they give weight to your site. When they see that you are not linking straight back to the site that linked you, that you don't have some sort of linking agreement going on, they give it more weight as a link. The assumption is that someone of their own free will linked to your content, and did not require you to link back to them to do it. If that is the case, then your content must be of high quality. Since one way links are so powerful, and don't require any ongoing maintenance, most linking strategies out there today revolve around one way links of some form.
Three Way Links
Three way links are a variation on reciprocal links. However instead of the 'You link to my site, I link to yours' idea, the correct term would be 'You link to my site, I link to yours from a different site of mine'. It's basically a reciprocal link, but your incoming link is coming from some 3rd site instead.
It is thought that the search engines don't particularly care much for three way linking. The thought is that you may be trying to fool the search engines into thinking you are getting a one way link from someplace, when its really just a reciprocal link in disguise. One use of three way linking that is common is for when you have 2 very popular sites, and one brand new one. The idea is that 'I link to your brand new, unpopular site from my very popular site, and instead of me linking back to you from my new site that isn't as popular. I will link to you from one of my other, very popular sites so you get a better weight with the search engines'. Three ways linking is fairly common, but I don't do it and I would not recommend it.
About The Author
The author is an Internet marketing consultant who specializes in link building services and search engine optimization techniques. Hence has shared some of its vital points through the article.
The author invites you to visit:
http://www.bookmarking-services.com
Article Source:
http://www.articlecity.com
Guidelines For Creating Proper Link Text
Let me explain what I mean about creating proper link text. Link text is just that, the text that the actual link is made from. I'm sure you have seen links just like 'Continue' numerous times in your travels. While having link text like that isn't going to prevent search engines or people from going to those links, it's definitely not helping with the search engines idea of what that linked page is about.
What’s Wrong with Them?
What’s wrong is that the links don't actually describe the pages that they are linking to. When the search engines come upon that link in their spidering, they are going to assume that the destination that the link leads to is about a subject called 'Click Here'. While modern search engines are smart enough to get around this and still figure out what the destination page is about, the link is a definite missed opportunity!
Why Does That Matter?
It matters because the link in the eyes of the search engine has given weight to the phrase 'Click Here' for your websites destination page. The search engine then realizes that 'Click Here' is not correct and most likely just excludes the phrase from being weighted. So you end up getting credit for the link itself, but not any of the words in the link. You could have loaded up the link with some nice juicy keywords instead!
Better Examples
A good link to this particular article could be something like 'Creating Good Link Text'. That basically sums up what this content is about. I have used the link text to describe what the subject of this page is. A good rule of thumb is to create a link text that is between 1-4 words long that describes best what your destination page is about. The search engines will give weight to this page for the term 'creating good link text' and I can imagine someone typing that exact phrase into a search engine. Then since my page is linked with that exact term, this page is more likely to appear high in the search rankings!
Mix It Up
One thing you will want to avoid is using the exact same link text over and over for a particular page. This means if I were to go and submit this page to a bunch of link directories, asked people to link to this page, or linked to this page from some of my other websites. I would not want to just keep using the phrase 'creating good link text' over and over. A better idea would be to mix it up with different variations. For instance I could use 'link text', 'link naming', 'link naming strategies', or other similar names that said the same thing, but used different words.
Have the basics of link text covered? Then be sure to do some research on more advanced linking topics, such as tips on placing text around your links, how many links to put on a page, and what to do when you have to use a name as the link (such as for blog comments).
About The Author
The author invites you to visit:
http://www.bookmarking-services.com
Article Source:
http://www.articlecity.com
Sunday, November 15, 2009
DBX File Corruption Due to Damaged Identity Registry Key
Dbx Recovery - In Microsoft Outlook Express, the Identities registry key contains a sub-key for every Identity. When you create an Identity, Microsoft Windows generates an extensive number, known as GUID (Global Unique Identifier), and creates the Identities sub-key with GUID for its name. In case of damage to these registry keys, your critical and valuable data from Outlook Express may become inaccessible and require dbx file Recovery to be sorted out.
Sometimes, when you attempt to access data from Microsoft Outlook Express account, you might encounter any of the following error message:
Msimn.exe has generated errors and will be closed by Windows. You will need to restart the program. An error log is being created.
Or
MSIMN caused an invalid page fault in module MSOE.DLL.
In such situations, all of your mission critical data becomes inaccessible and you need to opt to recover dbx files, it’s an Outlook Express Repair solution to work around this issue.
Root of the issue
You might encounter the above error message due to any of the below given reasons:
1-The Identities key of Outlook Express in Windows registry is corrupted. Corruption to the Identity registry key possibly damages the DBX file.
2-The DBX files of Outlook Express are marked as read only.
Resolution
There are two possible solutions to sort out this issue:
1- If the DBX files of MS Outlook Express are marked as read only, you can not access them. It could occur if you’ve recently restored files from backup. To access data in such situations, remove read only attribute of the DBX files.
2-If corrupted Identities registry key is causing this problem, regenerate it. This process requires you to modify the Windows registry. You should create backup of registry prior to modify it. After regenerating the Identity registry, restart Outlook Express to gain access of your data.
When all else fails, Outlook Express Recovery comes for your rescue. It is the process to repair and restore damaged DBX file and retrieve data from it using third party recovery applications. The recovery applications are capable of handling most of the DBX file corruption situations.
You can use the Outlook Express Repair tools, without having sound and prior technical skills as these software come equipped with interactive and simple graphical user interface. With read only and non destructive nature, these applications are complete safe to use.
Stellar Phoenix Outlook Express Recovery is the most powerful and effective tool to ensure absolute recovery of all your mission critical data from corrupted DBX file. It works well with Outlook Express 6.0, 5.5, 5.01 and 5.0. This software is designed for Windows Vista, XP and 2000.
For more information visit http://www.outlookexpress-recovery.com/
About The Author
Author has 6 Years of Experience in the Software Technology field working as a freelancer with Stellar which offers DBX Recovery Tool.
The author invites you to visit:
http://www.outlookexpress-recovery.com/
Article Source:
http://www.articlecity.com
What Exactly is Computer Memory and How Is it Used?
by: Sarah Phelt
Memory is one of the core hardware components for the computer. It is the component that temporarily stores information (such as Numbers, Characters, Settings, Instructions, Files and so on) once a computer has started. The information is temporary because when a computer is switched off or restarted the information is deleted from memory. When a program has finished with the information, the memory it was using is released (not deleted) so other programs can then use that memory.
Memory itself is a microchip (see above) that can temporarily store Bytes. The more bytes the memory has the more information it can temporarily store. A byte is just a number with a value between 0 and 255. It is a program's job to turn each byte into something a human and/or another program can interpret. For example. If the memory was storing 4 Bytes with the values 74, 79, 72 and 78 it would mean nothing to you. However. To Microsoft Word 2007 the byte value 74 means J. The byte value 79 means O. The byte value 72 means H and the byte value 78 means N. So even though the memory is storing byte values that mean nothing to you, Microsoft Word 2007 has no trouble interpreting (reading) those same byte values as JOHN. The same applies to other programs that interpret (read) the byte values. For example. A Paint program might interpret 74 as colour Red, 79 as colour Yellow, 72 as colour Blue and 78 as colour Green. Whereas a Language program might interpret (read) 74 as English, 79 as Spanish, 72 as French and 78 as Italian. It depends on the program. Either way, the memory will always see 74, 79, 72 and 78. Here is a diagram of the memory with the 4 Bytes interpreted.
The logic behind interpreting byte values is like so: If the byte value is 74 display J (Microsoft Word 2007). If the byte value is 74 use English (Language program). If the byte value is 74 use colour Red (Paint program). And so on. In other words, the byte will always have its value of 74 but it can be interpreted differently depending on the program doing the interpreting. Programs that save settings files use interpretation a lot to cut down on the number of bytes used. For example. If a paint program had to interpret RED, YELLOW and BLUE with characters it would use 13 Bytes (R E D Y E L L O W B L U E). Whereas using the logic of byte values to represent RED, YELLOW and GREEN it would only use 3 Bytes (79, 74 and 72).
Although the above concentrated on programs interpreting byte values that were already stored inside memory, the reverse is just as true. For example. When you type the word JOHN into a Microsoft Word 2007 document its stores (puts) the byte values 74, 79, 72 and 78 inside memory. The same with a paint program. Instead of storing the characters R E D (byte values 82, 69 and 68) it might store the byte value 74 (which represents RED in the above example) so that it is uses 1 Byte, instead of 3, every time you use the red ink.
Basically, memory is just full of numbers that are interpreted by programs to mean Instructions, Settings, Characters, Words, Sentences, Numbers, Symbols and so on.
ENOUGH MEMORY
When a program opens it first allocates some memory for its own needs. For example. If you open a 1000 bytes essay file with Microsoft Word 2007, from a floppy disk, and edit it (i.e you change the word JOHN into PAUL) the changes are not made to the essay file on the floppy disk. They are made inside memory instead, to avoid wear of the floppy disk. If you imagine every time you edited an essay character (byte value) the whole essay file had to be re-saved onto floppy disk you would soon end up with a damaged floppy disk. Just changing JOHN into PAUL would mean four re-saves. Memory is purposely made for the constant editing of byte values.
When Microsoft Word 2007 opens an essay file from floppy disk for example it first allocates (reserves) 1000 bytes of file memory, so it can store an exact copy of the essay file inside that memory - The original essay file on the floppy disk is left intact. The next thing Microsoft Word 2007 does is allocate some memory for its editing needs. For example. If you make a copy of the word JOHN, because you want to add (paste) it somewhere else in the essay, behind the scenes Microsoft Word 2007 makes a copy of the word JOHN by storing the word JOHN inside the edit memory. So you now have 1000 bytes full of essay characters inside the file memory and 4 bytes used inside the edit memory for the J O H N characters. However. Because you might want to copy a paragraph, an whole essay page or even the whole essay Microsoft Word 2007 has to make sure it has allocated enough edit memory for these situations. The same applies to the file memory - It might not be allocated just 1000 bytes for the essay characters, but perhaps 3000 bytes just in case you need to add more to the essay (i.e you start copying bits out of an History/Research file into the essay or you just type more characters into the essay). So the essay might need 5000 bytes in total allocated for it. Once you have finished editing the essay, which is in file memory at this point, you then tell Microsoft Word 2007 to save the file memory back onto the floppy disk as an essay file.
A collection of bytes is known as Data. Microsoft Word 2007 sees files and memory as a block of data only, which means when it opens a file and copies it into memory all it is doing is copying a block of data from one place (i.e Floppy Disk) to another (i.e Memory). So when it saves the essay file from file memory to floppy disk it just sees it as copying a block of data from one place to another. And that is how you should see files and memory - as blocks of data. Once the essay (file memory) has been saved onto the floppy disk as an essay file the file memory and edit memory are released for other programs to use.
The above is okay when everything is running smoothly, but problems arise when a program tries to allocate memory that is not available. For example. If you try to open too many programs or files at once they might crash (Freeze/Stop) Windows Vista. This would be due to the programs either not having enough memory to open themselves (i.e show their own windows) or not enough memory for their additional needs, such as editing files. For example. If there are only 10,000 bytes of memory remaining and two newly opened programs are waiting for 50,000 bytes of memory each they will be put in a waiting queue. Waiting forever. Or at least until another program closes and releases its memory, but it might only be releasing 4000 bytes of memory. In which case one of the waiting programs could use the 4000 bytes now available and then wait for the other 46,000 bytes to become available. On the other hand, the programs might get sick of waiting and decide to close. Either way it is a slow and messy process. This is why you should get to know the limits of your computer first before opening too many programs at once. Another scenario is memory corruption. Basically this is when a program misinterprets some byte values. For example. If a language program is supposed to read 74, in a settings file, as English but sees (reads) 77 instead. It would probably show text in a different language - Not much harm as you could probably change the language setting back to English once the language program had opened and fully completed. However. Imagine if a program interprets a byte value of 100 to mean you have paid/registered to use that program and a byte value of 101 to mean you are just trying out that program for 30 days. You might of paid £30 for a program that is saying you have not paid, but you are just trying it out. Incidently. This is one way hackers hack legal software...they change the software's data (byte values) so it thinks the user has paid for it. Apart from hacked bytes data is normally corrupted because the files (software/programs) came from a bad/scratched floppy disk or CD - The files can still be read as data (byte values), but as incorrect data. Unfortunately, a program will not test every byte value inside a file simply because it would take too long, especially if it was a large file.
BYTE SIZES
The reason for explaining memory to you is so that you get some idea of how Data is stored and how memory is allocated. In the above examples I mentioned bytes in terms of thousands only (i.e 4000 and 50,000) so you could understand the examples quite easily. However. The reality is that programs and files have become bigger and bigger over the years, to the point where you no longer say a file is just a few thousand bytes long. Now a file can be millions of bytes long. The same applies to the computer. Years ago the memory inside it might have been a maximum of 32KB (32768 bytes), whereas these days it must have a minimum of 256MB (262,144,000 bytes) inside it. KB, GB and MB are Byte terminology (jargon), as below:
Byte = 1 Byte
Bytes = 2 Bytes or more
1 KiloByte = 1,024 Bytes - KiloByte(s) is abbreviated to KB
2 KiloBytes = 2,048 Bytes - To work out KiloBytes just devide or multiply Bytes by 1,024
1 MegaByte = 1,024,000 Bytes - MegaByte(s) is abbreviated to MB
2 MegaBytes = 2,048,000 Bytes - To work out MegaBytes just devide or multiply Bytes by 1,024,000
1 GigaByte = 1,024,000,000 Bytes - GigaByte(s) is abbreviated to GB
2 GigaBytes = 2,048,000,000 Bytes - To work out GigaBytes just devide or multiply Bytes by 1,024,000,000
READ / WRITE
When data is being read (i.e from a floppy disk) it is known as Reading the data (because it is being looked at) and when data has been read it is known as Read (because it has been looked at).
When data is being saved it is known as Writing the data (because it is being written onto something, such as: a floppy disk) and when data has been saved it is known as Written (because it has been written onto something, such as: a floppy disk).
ROM / RAM
Memory is known by two types. ROM (Read Only Memory) which means hardware and software can only read the byte values stored inside rom memory and RAM (Read Access Memory) which means hardware and software can not only read the byte values stored inside ram memory but they can also, temporarily, change the byte values stored inside ram memory.
ROM memory is a microchip on a motherboard (green microchip board), such as a Modem motherboard, that contains the instructions (byte values) needed to make the hardware (Modem) work. This is why ROM memory cannot have its byte values changed. The instructions (byte values) are preprogrammed onto the microchip, so that when you first switch on the computer the instructions (byte values) are always the same.
RAM memory is a microchip that is permanently fitted onto a Card (small motherboard), such as a Graphics Card or Memory Card, or a single removable microchip that you attach to the main motherboard. The main motherboard is the big green microchip board inside the computer (base unit). RAM memory can have its byte values temporarily changed, and read, so that you can change Graphics settings (Graphics Card) or store data (Memory Card) for example. Even though RAM memory is cleared when you switch off or restart the computer, because it is meant as a temporary storage place only, the data inside the memory is normally saved by a program (as a file) beforehand. For example. If you change the Modem (hardware) settings using a modem program it will save your changes as a settings file on the hard drive before the computer is switched off or restarted. When the computer is switched on again the modem uses its default (normal, preprogrammed) settings before looking at, and using, the settings from the saved settings file. The modem uses its default settings first for two reasons. One is so that it knows it is setup correctly (by using its normal, manufacturer's, preprogrammed settings) and two is in case the settings file is corrupt, damaged or missing. If it reads a settings file incorrectly (i.e because it is corrupt) you may get problems with the modem or it may revert back to its default settings.
VIRTUAL MEMORY
When Windows Vista finally runs out memory, or when it cannot fit something really big inside memory as one piece, it starts using a thing called Virtual Memory, which is Hard Drive space that is used as memory. For example. Imagine you have just typed out a 10,000 line document using Microsoft Word 2007 and then you run out memory. Instead of Windows Vista telling you "You cannot type anything else - No more Memory available" it will just let you carry on typing as normal. This is because the rest of your typing will be stored on the hard drive as a file, which you have no access to. As far as you are concerned you are just typing a document and so do not have to worry about virtual memory. However. You should be aware that over time this wears out the hard drive. So always make sure you have plenty of memory.
GRAPHICS MEMORY
Graphics Memory is the memory that stores your Imagery (Desktop Picture, Game Scenes, Photographs, Icons, Text and so on). It is a microchip on the Graphics Card. The main job of a graphics card is to store Imagery inside its graphics memory and then display that imagery, on the monitor screen, when a program asks it to. For example. If you are editing a photograph the paint package would of allocated some of the graphics memory as file memory (for the original photograph) and some of the graphics memory as edit memory (for editing purposes) - In the same way the file memory and edit memory was allocated in the Microsoft Word 2007 explanation above. The graphics card will not only display the photograph (file memory) on the monitor screen, but it will also update (refresh) the monitor screen instantly every time you edit the photograph. In the same way that Microsoft Word 2007 updates instantly any changes you make to a document. Graphics memory is also in charge of storing other imagery. For example. If you have one game open, a paint program open and the Internet open it is graphics memory storing the imagery of those three programs. The more programs open that use graphics memory the more tasks (jobs) you are giving the graphics card. Meaning. If you give it too much to do and/or it runs out of graphics memory it will not be able to update the monitor screen quick enough, which means editing and game playing for example will not be instant. The monitor screen will update (draw the imagery) so slowly that it would not be worth editing a photograph or playing a game. A normal sign of this is when the monitor screen is updated (drawn) line by line as opposed to instantly. So get a good Graphics Card with plenty of Graphics Memory because the one built into the computer might not be good enough for your needs.
MEMORY SPECIFICATIONS
Memory Size is measured in multiples of 8 MegaBytes (i.e 256MB, 512MB and 1024MB), which means you could never have 274MB or 519MB for example, and Memory Speed is measured in MegaHertz (Mhz).
Computers made before the year 2000 normally use memory known as SDRAM, which is now difficult to find because it is no longer manufactured. A SDRAM memory chip can either be 100Mhz, 133Mhz or 166Mhz and is named after its speed: PC100, PC133 or PC166.
Computers made between the years 2000 to 2005 (approximately) normally use memory known as DDR, which is still being sold at the present time. A DDR memory chip normally comes with one of the following specifications: PC1600 (200 Mhz), PC2100 (266 Mhz), PC2400 (300 Mhz), PC2700 (333 Mhz), PC3200 (400 Mhz) or PC4000 (500 Mhz).
Computers made between the years 2005 to 2008 (approximately) normally use memory known as DDR 2, which is currently the main type of memory sold. A DDR 2 memory chip normally comes with one of the following specifications: PC2-3200 (400 Mhz), PC2-4200 (533 Mhz), PC2-5300 (667 Mhz) or PC2-6400 (800 Mhz).
Note. As newer/better memory is manufactured every so often the memory specifications above are just to give you an idea of the kind of memory specifications available - I have not mentioned every single memory specification out there in other words. The time overlaps above (i.e. in 2005) mean that newer memory was created in the same year.
As most computers, regardless if old or new, only have two memory slots inside them it is wise to have at least 512MB in each slot. Using anything less is just going to make the computer slow. For example. The minimum memory requirement for Windows XP used to be 256MB only, but now that many programs like Windows Media Player have improved and use more memory it means Windows XP's minimum memory requirement is now 512MB. Remember. This is minimum. You should always aim for the maximum.
Here are the minimum requirements for 2009.
Windows XP - 768 MegaBytes (1.5GB or more recommended)
Windows VISTA - 1.5 GigaBytes (2GB or more recommended)
Article Source:
http://www.articlecity.com
About The Author
http://www.yoingco.com
FREE Website Creation Help
http://www.websitecreationhelp.com